Web Service Integration
Disclaimer
Your use of this download is governed by Stonebranch’s Terms of Use, which are available at Stonebranch Integration Hub - Terms of Use.
Version Information
| Template Name | Extension Name | Extension Version |
|---|---|---|
| Web Service Integration | ue-webservice | 1.4.1 |
Refer to the Changelog for version history information.
Overview
A Web service is a method of communication between two electronic devices over a network. This Universal Extension provides the capability to call endpoints of foreign APIs. It is beneficial for Stonebranch SaaS customers that are accessing the Universal Controller in the Stonebranch AWS Cloud and having their Universal Agents deployed in their data center. As the integration is triggered from the Universal Agent, no additional firewall port for the Universal Agent needs to be opened.
Key Features
Feature | Description |
|---|---|
Send HTTP(S)/REST requests | This integration supports sending requests over HTTP(S)/REST protocol, using the following methods:
|
Connectivity and Authentication Options | A variety of authentication options are supported:
Additionally, a Proxy server can be configured to be used between the Universal Agent and target endpoint. |
Custom exit code processing | This integration provides the capability to the user, to configure custom exit codes based on the web service response payload (Supported for JSON payloads). |
Requirements
This integration requires a Universal Agent and a Python runtime to execute the Universal Task.
Area | Details |
|---|---|
Python Version | Requires Python 3.7. Tested with the Universal Agent bundled Python distribution (version 3.7.16) |
Universal Agent | Both Windows and Linux agents are supported:
|
Universal Controller | Universal Controller Version >= 7.2.0.0. |
Network and Connectivity | The Universal Agent needs to have connectivity to the Web Service endpoint, and Access Token endpoint in case Authentication Type is “OAuth 2.0” and Proxy if the connection is through a Proxy. |
Supported Actions
This integration is responsible for sending HTTP(S)/REST requests.
Configuration examples
The following examples demonstrate the available authentication types, combined with some of the key features of this integration.
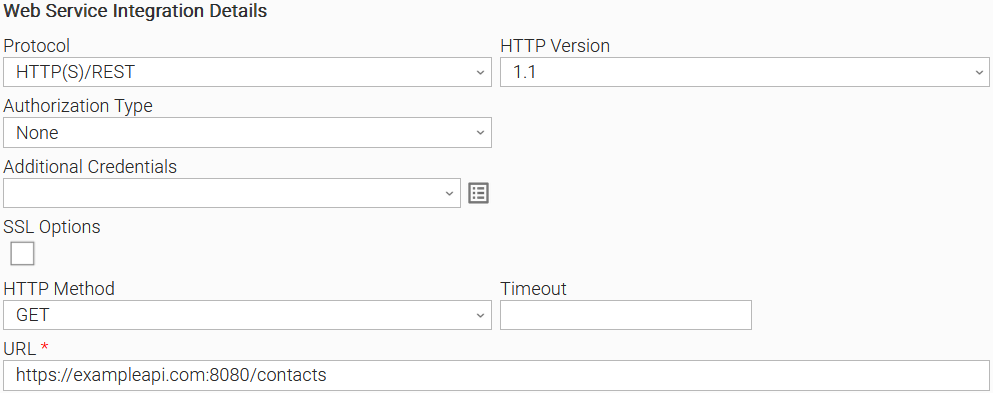
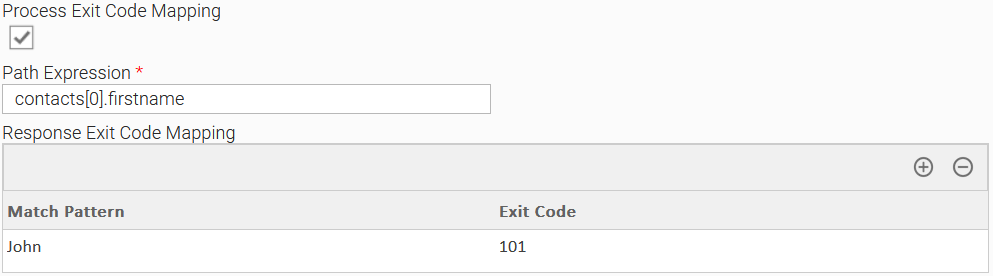
Example 1: No Authorization With Exit Code Mapping Task Configuration
Example of Universal Task for "None" Authorization Type where the user expects an exit code equal to "101" if the employee's first name is "John".
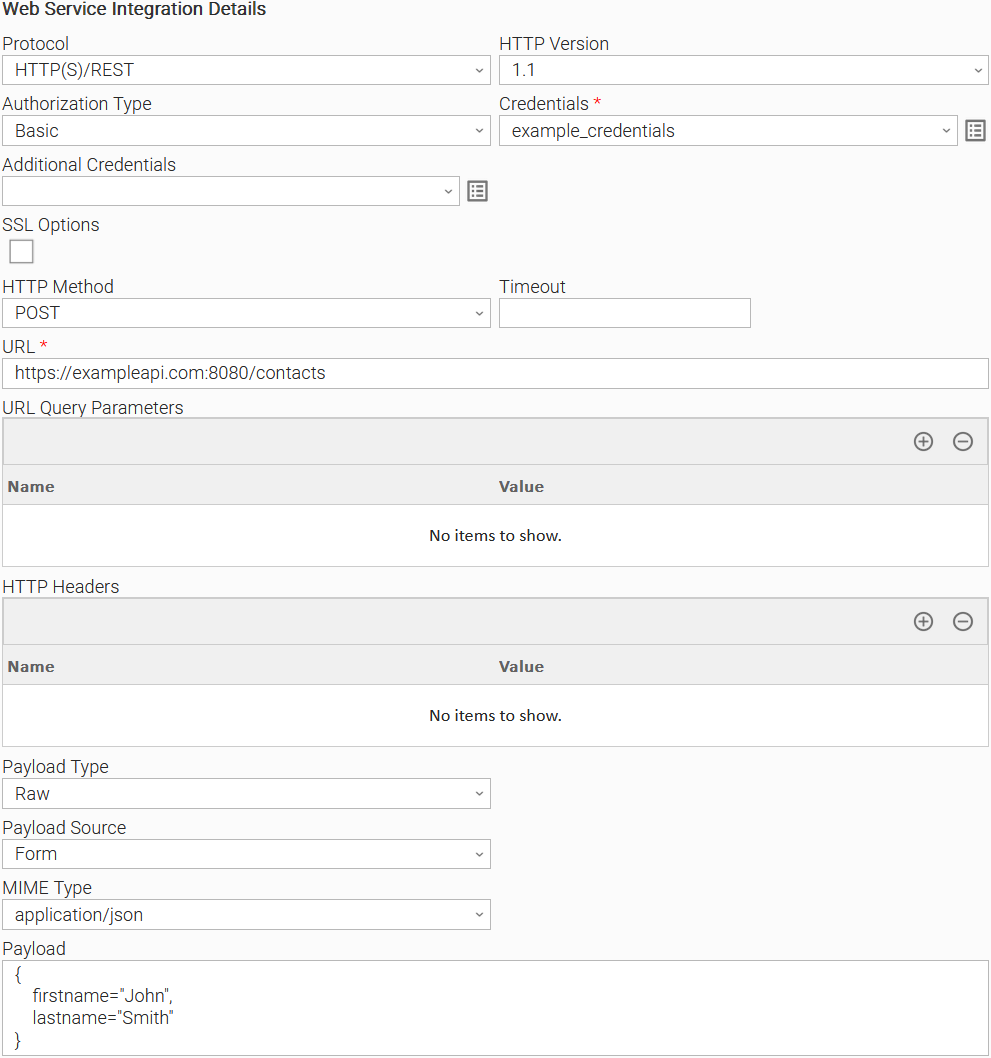
Example 2: Basic Authorization Task Configuration for a POST request with JSON payload
Example of Universal Task for "Basic" Authorization Type.
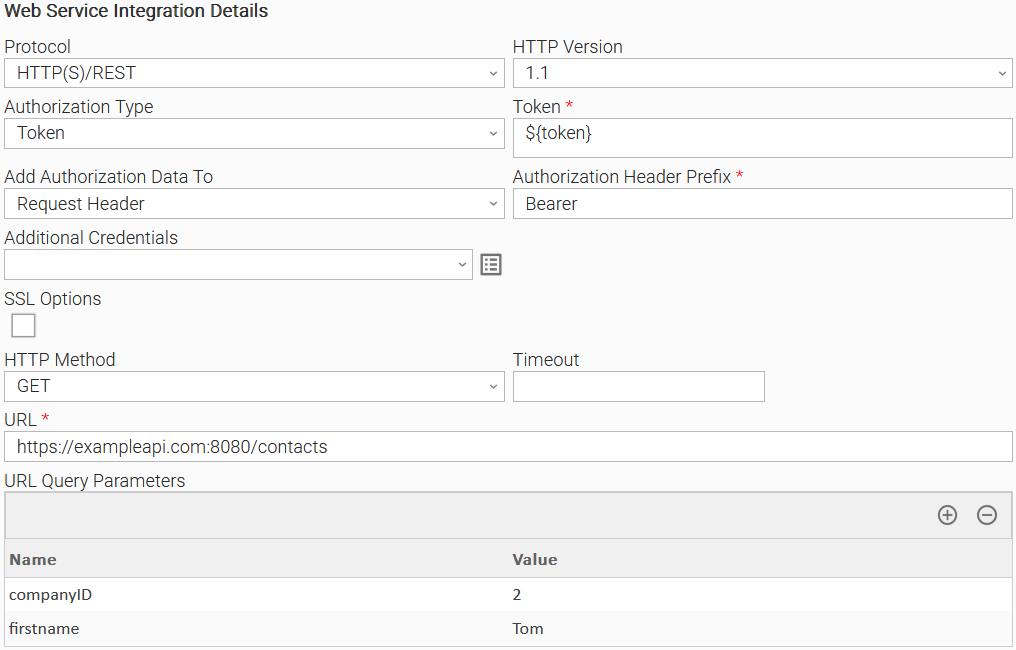
Example 3: Token Authorization Task Configuration with URL Query parameters
Example of Universal Task for "Token" Authorization Type with URL Query parameters.
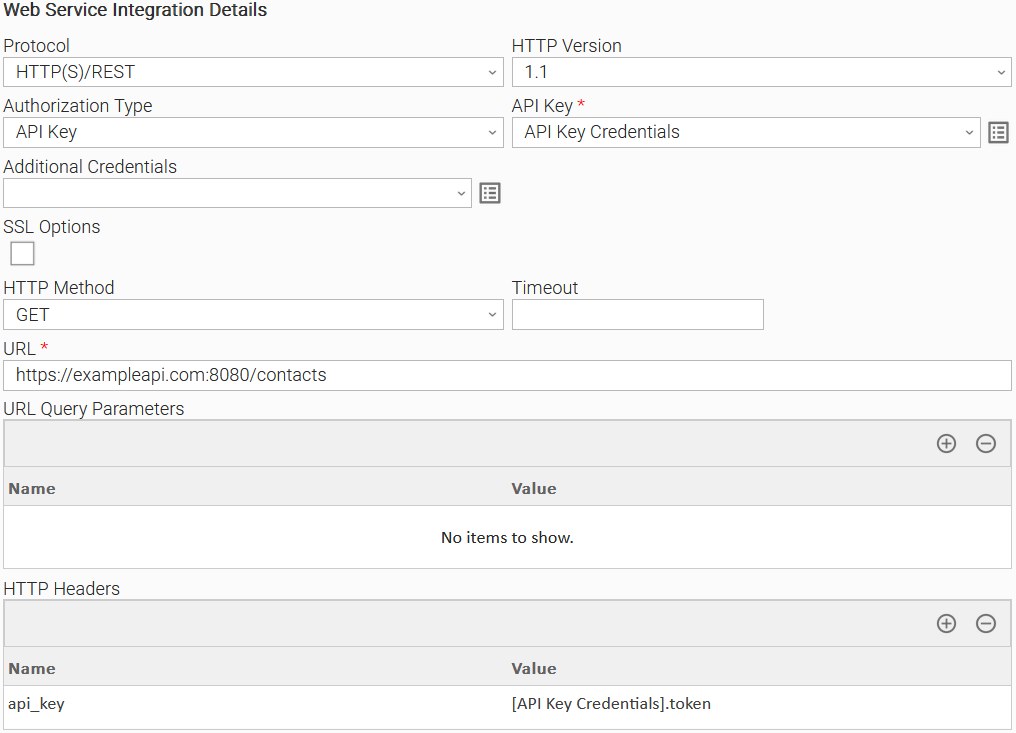
Example 4: API Key Authorization Task Configuration
Example of Universal Task for "API Key" Authorization Type.
To see how to pass the API Key as HTTP Header refer to Passing Credentials as Query Parameters, Headers, or as Form Data.
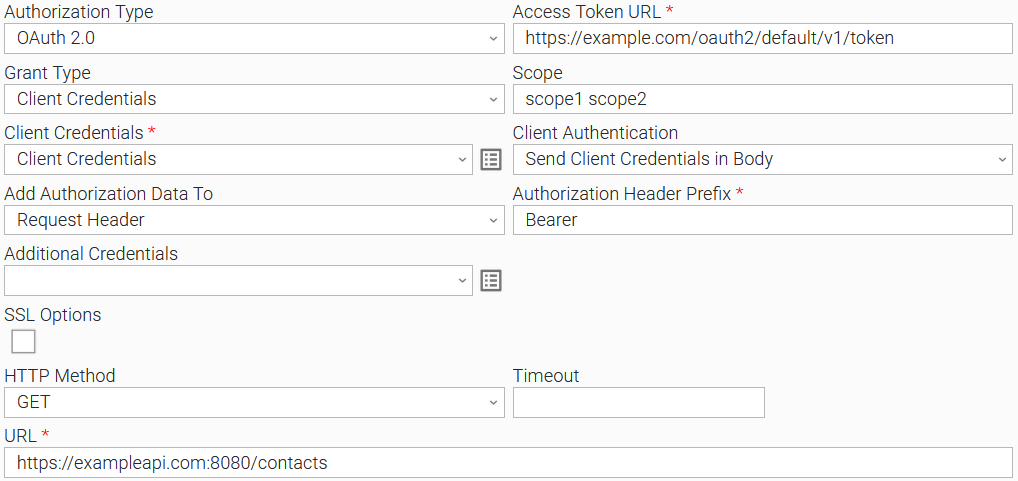
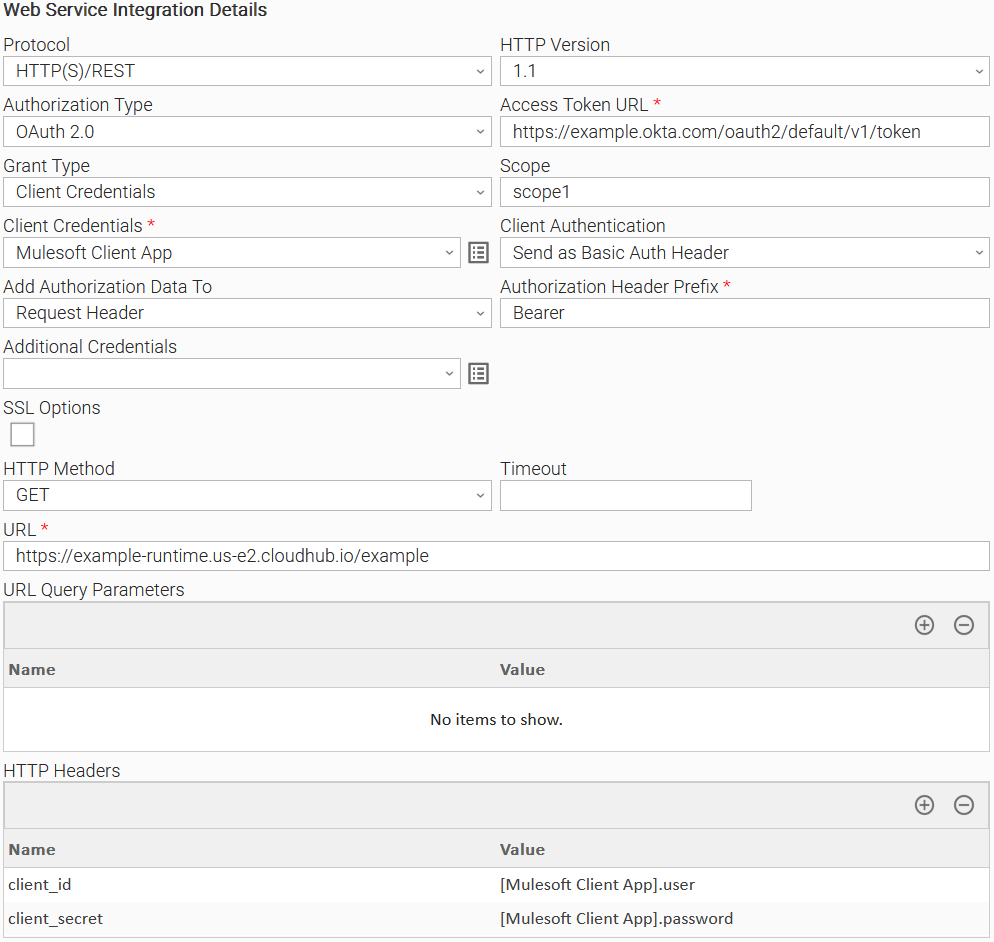
Example 5: OAuth2.0 Authorization Task Configuration
Example of Universal Task for "OAuth2.0" Authorization Type with client credentials grant type.
To see how to pass credential fields as HTTP Headers refer to Passing Credentials as Query Parameters, Headers, or as Form Data.
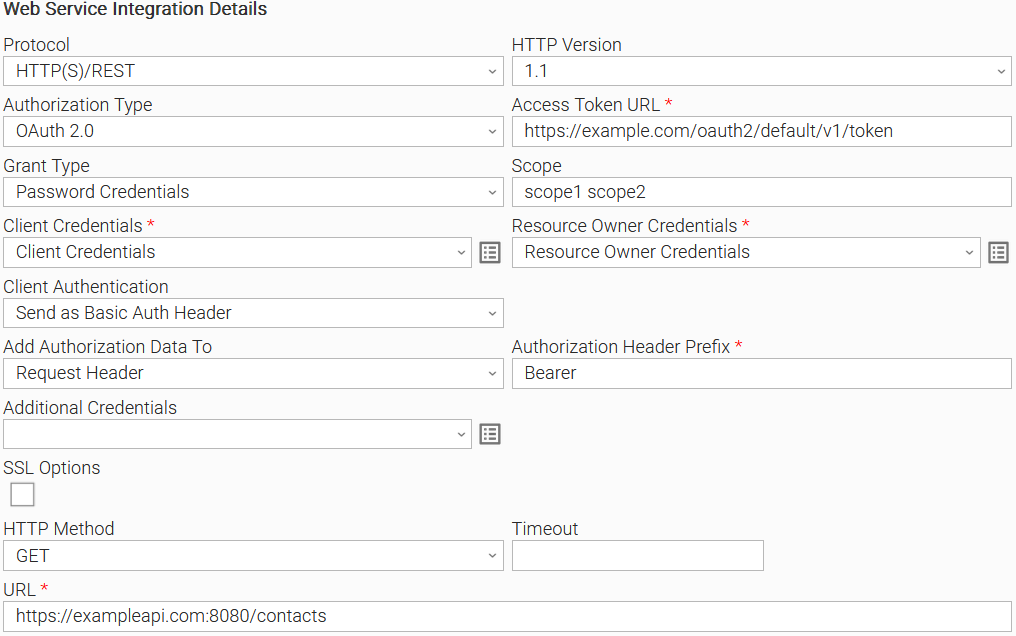
| User Scenario: Example of Universal Task for "OAuth2.0" Authorization Type with client credentials grant type | User Scenario: Example of Universal Task for "OAuth2.0" Authorization Type with password credentials grant type. |
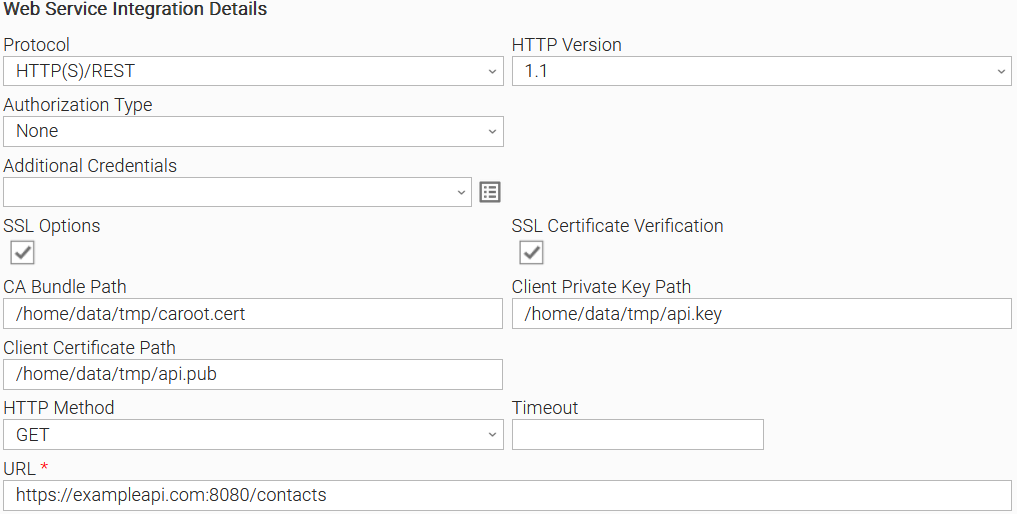
Example 6: Task Configuration with SSL Client Authentication
Example of a Universal Task with SSL Client Authentication.
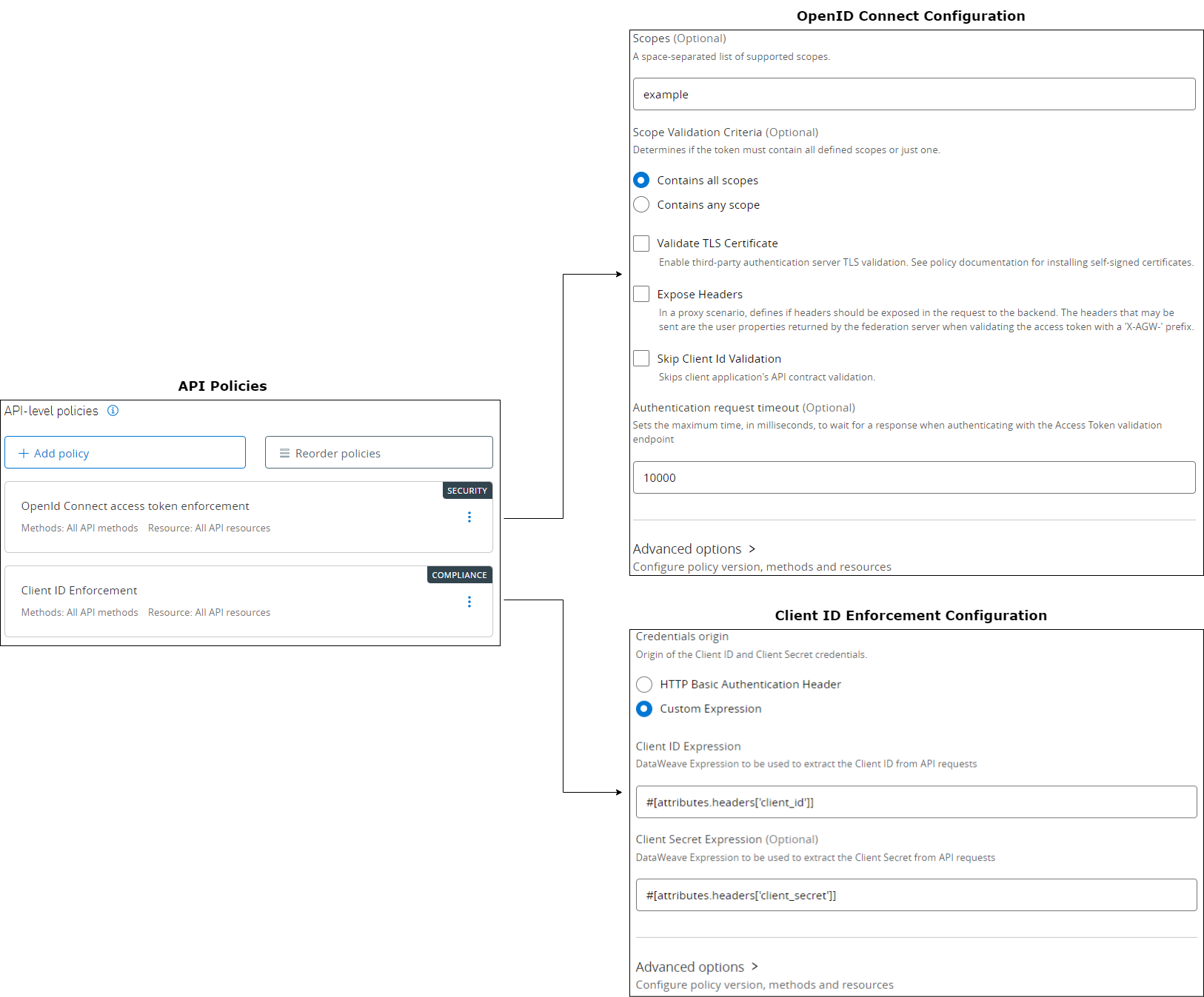
Example 7: Mulesoft
The following example shows the configuration of a task for a call to a Mulesoft API that has OpenID Connect access token enforcement and Client ID Enforcement policies enabled and when Okta is used as a Client Provider. OAuth2 Client Credentials flow is used in the following example.
Task Configuration
As it's evident from the Client ID enforcement configuration, Client Credentials are also passed as HTTP Headers.
To see how to pass the client credentials as HTTP Headers refer to Passing Credentials as Query Parameters, Headers, or as Form Data.
Action Output
Output Type | Description (Successful Execution) | Example (Successful Execution) |
|---|---|---|
EXTENSION | The extension output provides the following information:
| {
"exit_code": 0,
"status_description": "Task executed successfully.",
"invocation": {
"fields": { ...
},
},
"result": {
"code": 200,
"headers": [
{
"header": "Content-Encoding",
"value": "gzip"
},
{
"header": "Content-Type",
"value": "application/json"
},
{
"header": "Display",
"value": "staticcontent_sol, orig_site_sol"
},
{
"header": "Response",
"value": "200"
},
{
"header": "Vary",
"value": "Accept-Encoding,User-Agent,Origin"
},
{
"header": "Transfer-Encoding",
"value": "chunked"
}
],
"body": "{\"status\":\"success\",\"data\":[{\"id\":1,\"employee_name\":\"Tiger Nixon\",\"employee_salary\":320800,\"employee_age\":61,\"profile_image\":\"\"},
{\"id\":2,\"employee_name\":\"Garrett Winters\",\"employee_salary\":170750,\"employee_age\":63,\"profile_image\":\"\"}",
"body_json": {
"status": "success",
"data": [
{
"id": 1,
"employee_name": "Tiger Nixon",
"employee_salary": 320800,
"employee_age": 61,
"profile_image": ""
},
{
"id": 2,
"employee_name": "Garrett Winters",
"employee_salary": 170750,
"employee_age": 63,
"profile_image": ""
}
]
}
}
|
STDOUT | If the field “Print Result Body To” is set to STDOUT, the body of the response will be printed here. | {
"status": "success",
"data": [
{
"id": 1,
"employee_name": "Tiger Nixon",
"employee_salary": 320800,
"employee_age": 61,
"profile_image": ""
},
{
"id": 2,
"employee_name": "Garrett Winters",
"employee_salary": 170750,
"employee_age": 63,
"profile_image": ""
}
}
|
Input Fields
Field | Type | Default value | Required | Description | Introduced In Version |
|---|---|---|---|---|---|
Protocol | Choice | HTTP(S)/REST | Required | The communication protocol to be used towards the foreign API. | |
HTTP Version | Choice | 1.1 | Required | The Hypertext Transfer Protocol version. | |
Authorization Type | Choice | Basic | Required | The authorization type to be used for communicating with the foreign API. The following options are available.
| |
Credentials | Credentials | - | Optional | Credentials for "Basic" Authorization Type. The Credentials definition should be as follows.
Required when Authorization Type is "Basic". | |
API Key | Credentials | - | Optional | Credentials for “API Key” Authorization Type. API Key should either be stored as the “Password” or “Token” Credential attribute, during Credential definition. Required when Authorization Type is “API Key”. | Introduced in version 1.3.0 |
Grant Type | Choice | Client Credentials | Optional | The OAuth 2.0 Grant Type used to get the token. Supported Grant Types are the following.
Required when Authorization Type is "OAuth 2.0". | Introduced in version 1.3.0 |
Access Token URL | Text | Optional | The endpoint of the Authentication Server for the retrieval of access token. It is used to exchange the Client Credentials (and the Resource Owner Credentials in the case of "Password Credentials" Grant Type) for an access token. Required when Authorization Type is "OAuth 2.0". | Introduced in version 1.3.0 | |
Scope | Text | - | Optional | A space-separated list of scopes used during retrieval of an OAuth 2.0 access token. Required when Authorization Type is "OAuth 2.0". | Introduced in version 1.3.0 |
Client Credentials | Credentials | - | Optional | Used for retrieval of OAuth 2.0 access token. The Credential definition should be as follows.
Required when Authorization Type is "OAuth 2.0". | Introduced in version 1.3.0 |
Resource Owner Credentials | Credentials | - | Optional | Used for retrieval of OAuth 2.0 access token. The Credential definition should be as follows.
Required when Grant Type is "Password Credentials". | Introduced in version 1.3.0 |
Client Authentication | Choice | Send Client Credentials in Body | Optional | Controls whether the Client Credentials are sent in the request body or as a basic authentication header during retrieval of OAuth 2.0 access token. The following options are available.
Required when Authorization Type is "OAuth 2.0". | Introduced in version 1.3.0 |
Token | Large Text | - | Optional | The authentication access token. Required when Authorization Type is "Token". | |
Add Authorization Data To | Choice | Request Header | Optional | Specifies where to include the Token in the request. The following options are available.
Required when Authorization Type is "Token" or "OAuth2.0". | |
Authorization Header Prefix | Text | Bearer | Optional | The prefix for the Token. The token value is appended to the Authorization Header Prefix in the request Authorization header. For example: Bearer <token_value>. Required when Add Authorization Data To is "Request Header". | |
Additional Credentials | Credentials | - | Optional | Additional credentials that might be required to be used either as Query Parameters or as HTTP Headers. For more information on how to pass credentials as part of URL Query Parameters refer to Passing Credentials as Query Parameters, Headers, or as Form Data. | Introduced in version 1.3.0 |
URL | Text | - | Required | The URL to be called. | |
HTTP Method | Choice | GET | Required | The HTTP method to be used in the request. The following options are available.
| |
Timeout | Integer | - | Optional | The time (in seconds) that the request will wait for the server to send data before closing the connection. If Timeout is not filled, the request will wait (hang) until the connection is closed. | |
URL Query Parameters | Array | - | Optional | The list of parameters key/value pairs to be sent in the query string for the request. | |
Payload Type | Choice | Raw | Optional | The type of data to be sent in the request body. The following options are available.
Required when HTTP Method is "POST", "PUT" or "PATCH". | |
Payload Source | Choice | Form | Optional | For Payload Type of value "Raw", it specifies how the payload will be provided. The following options are available.
Required when Payload Type is "Raw". | |
MIME Type | Choice | application/json | Optional | The MIME type to be used in the request's header. The following options are available.
Required when Payload Type is "Raw". | |
Other Value For MIME Type | Text | - | Optional | The MIME type to be included in request's header in case "Other" is selected as MIME Type value. Required when MIME Type is "Other". | |
Form Data | Array | - | Optional | The list of parameters key/value pairs to be sent in the request body. The request header will include ""x-www-form-urlencoded" as a "Content-Type" in this case. | |
Payload | Large Text | - | Optional | The payload to be sent in the request body. Required when Payload Source is "Form". | |
Payload Script | Script | - | Optional | The script to be used as a payload source. Required when Payload Source is "Script". | |
HTTP Headers | Array | - | Optional | The list of HTTP Headers key/value pairs to be sent with the request. If "Content-Type" header is provided, it will be disregarded by the extension, as the MIME Type field is used for this purpose. | |
Proxies (Deprecated) Deprecated in version 1.4.0 | Text | - | Optional | The field is deprecated. For backward compatibility reasons, the field is kept and functioning as of version 1.3.1. However, it is strongly advised to migrate the task definition to the new logic to avoid disruptions in the future. For more information refer to Set Proxies with Environment Variables and Known Issues. | |
SSL Options | Boolean | False | Required | Displays the available SSL options. | |
SSL Certificate Verification | Boolean | True | Optional | Enables certificate verification. Certificate verification is auto-enabled in case field "CA Bundle Path" field is populated. Required when SSL Options is checked. | |
CA Bundle Path | Text | - | Optional | Path and file name of the Certificate Authority bundle to use in certificate verification. The file should be in PEM format. | |
Client Private Key Path | Text | - | Optional | Path and file name of the private key file for SSL client-side authentication. The file must be in PEM format. | |
Client Certificate Path | Text | - | Optional | Path and file name of the public key certificate for SSL client-side authentication. The file must be in PEM format. | |
Print Result Body To | Choice | STDOUT | Optional | Specifies where to print the web service output payload. The following options are applicable.
| Introduced in version 1.1.0 |
Process Exit Code Mapping | Boolean | False | Required | The flag that determines whether exit code mapping is enabled or not. | Introduced in version 1.1.0 |
Path Expression | Choice | - | Optional | Field visible only when Process Exit Code Mapping is checked and it is required when visible. The JSON path which is used to check the provided patterns that are set up on the Response Exit Code Mapping array. | Introduced in version 1.1.0 |
Response Exit Code Mapping | Array | - | Optional | Field visible only when Process Exit Code Mapping is checked and it is required when visible. An array that maps regular expression patterns to exit codes. Provided exit codes should be in the range [100-255]. | Introduced in version 1.1.0 |
SSL Certificate Authority File Discovery
This Universal Extension is bundled with certifi library, utilized as the default certificate discovery mechanism. However, more complex SSL verification scenarios are supported, according to the configured fields as described below.
Server SSL verification by default CA
Certifi provides a wide range of certificates signed by well-known Certificate Authorities, used for SSL Server verification.
Related Universal Task fields:
- SSL Options: Enabled
- SSL Certificate Verification: Enabled
Server SSL verification by custom CA
For SSL Server verification against hosts that have certificates signed by a custom Certificate Authority, a Certificate Authority Bundle should be provided as input.
Related Universal Task fields:
- SSL Options: Enabled
- SSL Certificate Verification: Enabled
- CA Bundle Path: Populated
SSL Client Authentication
An additional security layer can be achieved with two-way SSL verification, where both the Server is verified by the Client, and the Client is verified by the Server. This scenario is common for hosts with self-signed certificate.
Related Universal Task fields:
- SSL Options: Enabled
- SSL Certificate Verification: Enabled
- CA Bundle Path: Populated
- Client Certificate Path: Populated
- Client Private Key Path: Populated
When the communication between the client and the server is based on HTTPS and SSL Certificate Verification is not enabled, communication is still encrypted. However, certificates are not verified. An appropriate warning is printed on the STDERR output
Exit Code Mapping
As part of task configuration, it is possible for the user to define custom exit codes that depend on the contents of the web service response body.
This might be useful in the following cases:
When the task is used in a workflow and based on the contents of the web service response body the workflow needs to follow a different path. Exit codes can be used in workflows to follow different branches.
When retry needs to be configured, based on the content of the web service response body. Task retry can be configured based on the exit code.
For example, a user can configure the Universal Controller task to retry execution when the exit code is X. Exit code X can be configured by the user when the web service response payload field JSON "document.status" is equal to value "Under Processing".
The fields related to this functionality are the following.
Process Exit Code Mapping
Should be checked to enable this functionality.Path Expression
The JSONPath expression (JSONPath Syntax).Response Exit Code Mapping
A list of pairs (Pattern/Exit Code). If the pattern provided as python regular expression is matched, then the configured exit code will be applied.
The web service output JSON body is parsed with the Path Expression. The matched response body content is evaluated against the list of patterns provided on Response Exit code Mapping array. When a pattern is matched, the extension will return the respective exit code.
The following features and restrictions are applied.
It is possible to provide multiple pairs of Pattern/Exit Code. The extension will return the corresponding exit code, on the first match in the array.
Provide
.*as a pattern, to match any value returned by the JSONPath.Provided exit codes should be between 100 and 255.
An error will be raised in case:
No match found.
A Wrong Path Expression is provided.
The result body is not of type JSON.
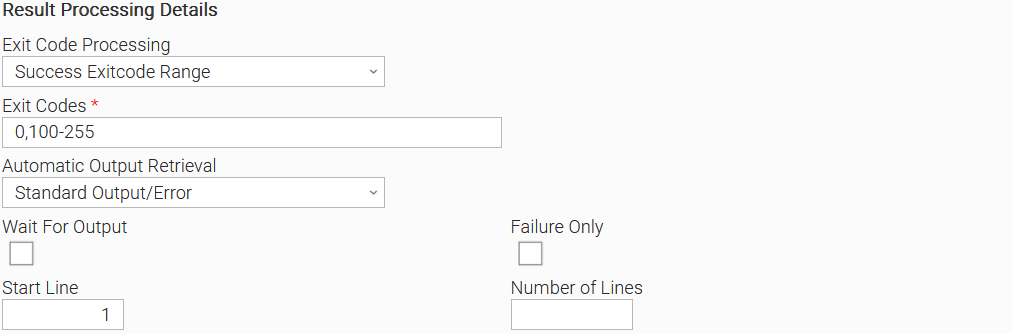
The custom exit codes that intend to be considered successful, have to be configured appropriately in the Result Processing Details section.
Exit Code Processing
Option "Success Exit Code Range" to be selected in this field.Exit Codes
To be filled with the list of exit codes that the user expects to reflect successful execution (Ranges can be provided. For example 0,100-255).
Passing Credentials as Query Parameters, Headers, or as Form Data
There are cases where the endpoint might require credentials to be passed either as part of Query Parameters, as Headers or in a URL-encoded form. For example, Mulesoft APIs can include Client ID Enforcement Policy for which a Client ID and a Client Secret are mandatory to be passed on top of other authorization/authentication inputs.
Additional Query Parameters can be passed through the "URL Query Parameters" field, additional HTTP Headers can be passed through the "HTTP Headers" field and form data can be passed through the "Form Data" field. All of them are Array fields. Array "Name" represents the Query Parameter Name, the Header Name, or the Form Data Key, and "Value" represents the value to be used. “Value” could be a specific string, or be in the format of [credential_name].attribute where
credential_name:The name of a Credential which is selected by a Credential field used in the task. Only Credential names that are selected in the task's credential fields can be used.attribute:The attribute of the specific Credential with possible values being the following.user
password
passphrase
token
If the provided credential_name is a valid Credential name and attribute is in the above domain, then a match is found and the specific Credential attribute is used. Else the provided input is used as a literal string.
Example: Let's suppose that a credential with name = "valid_credential_name" and password = "example_pass" is passed to a task. The expression [valid_credential_name].password will be resolved to example_pass.
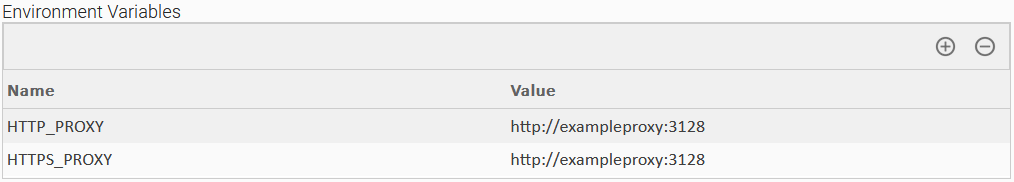
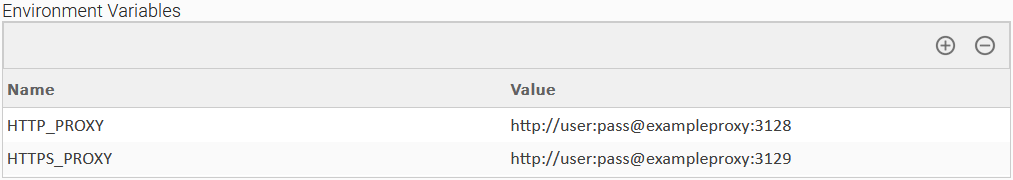
Set Proxies with Environment Variables
If a proxy is required to route the traffic between the Universal Task and the configured endpoint, then HTTP_PROXY and/or HTTPS_PROXY environment variables need to be set. HTTP_PROXY environment variable defines the proxy used in case of HTTP communication between the Universal Task and the endpoint, while the HTTPS_PROXY environment variable defines the proxy used in case of HTTPS communication between the Universal Task and the endpoint. In the majority of cases, only one proxy is used that routes both HTTP and HTTPS traffic (in such cases HTTP_PROXY/HTTPS_PROXY environment variables point to the same value).
The format is explained by the following examples.
Configuration Examples
| User Scenario: Passing a single proxy for HTTP and HTTPS traffic | User Scenario: Passing different proxies with credentials for HTTP and HTTPS traffic |
Output Fields
Field | Type | Description | Introduced in Version |
|---|---|---|---|
Response Code | Text | The webservice response code. | Introduced in version 1.0.0 |
Exit Codes
The exit codes for this Universal Extension are described in the following table.
Exit Code | Status Classification Code | Status Classification Description | Status Description |
|---|---|---|---|
0 | SUCCESS | Successful Execution | SUCCESS: Task executed successfully <Additional information>. |
1 | FAIL | Failed Execution | FAIL: <Unexpected error description> |
3 | AUTHORIZATION_ERROR | Insufficient Permissions | AUTHORIZATION_ERROR: The authorization credentials provided for the request are invalid. |
21 | FOREIGN_API_REQUEST_ERROR | Bad request to third-party API | FOREIGN_API_REQUEST_ERROR: Client side error when sending the request. |
22 | FOREIGN_API_RESPONSE_ERROR | Validation error response from third-party API | FOREIGN_API_RESPONSE_ERROR: Server side error. |
23 | FOREIGN_SERVER_ERROR | Destination URL not found or redirected | FOREIGN_SERVER_ERROR: Not Found |
24 | EXIT_CODE_MAPPING_ERROR | An error occurred during Exit Code Mapping | EXIT_CODE_MAPPING_ERROR: Invalid Path Expression |
STDOUT and STDERR
STDOUT and STDERR provide additional information to User. The populated content can be changed in future versions without notice. Backward compatibility is not guaranteed.
How To
Import Universal Template
To use the Universal Template, you first must perform the following steps.
This Universal Task requires the Resolvable Credentials feature. Check that the Resolvable Credentials Permitted system property has been set to true.
To import the Universal Template into your Controller, follow these instructions.
When the files have been imported successfully, refresh the Universal Templates list; the Universal Template will appear on the list.
Modifications of this integration, applied by users or customers, before or after import, might affect the supportability of this integration. For more information refer to Integration Modifications.
Configure Universal Task
For a new Universal Task, create a new task, and enter the required input fields.
Integration Modifications
Modifications applied by users or customers, before or after import, might affect the supportability of this integration. The following modifications are discouraged to retain the support level as applied for this integration.
Python code modifications should not be done.
Template Modifications
General Section
"Name", "Extension", "Variable Prefix", "Icon" should not be changed.
Universal Template Details Section
"Template Type", "Agent Type", "Send Extension Variables", "Always Cancel on Force Finish" should not be changed.
Result Processing Defaults Section
Success and Failure Exit codes can be changed according to users' needs.
Fields Restriction Section
The setup of the template does not impose any restrictions. However, with respect to the "Exit Code Processing" section.Success/Failure exit codes need to be respected.
In principle, as STDERR and STDOUT outputs can change in follow-up releases of this integration, they should not be considered as a reliable source for determining the success or failure of a task.
Users and customers are encouraged to report defects, or feature requests at Stonebranch Support Desk.
Document References
This document references the following documents.
| Document Link | Description |
|---|---|
| Universal Templates | User documentation for creating, working with and understanding Universal Templates and Integrations. |
| Universal Tasks | User documentation for creating Universal Tasks in the Universal Controller user interface. |
Known Issues
- The "proxies" field does not work correctly in some cases. Task authors are advised to use HTTP_PROXY and HTTPS_PROXY environment variables on task definition, or alternatively set those variables on the runtime user environment, leaving this field empty. For more information refer to Set Proxies with Environment Variables.
Changelog
ue-webservice 1.4.1 (2023-10-18)
Fixes
Fixed:Fix URL validation introduced on 1.3.0 (#34401)
ue-webservice 1.4.0 (2023-07-26)
Deprecations and Breaking Changes
Deprecated: "Proxies" field is deprecated. For backward compatibility reasons, the field is kept and functioning as of version 1.3.1. However, it is strongly advised to migrate the task definition to the new logic to avoid disruptions in the future. For more information refer to Set Proxies with Environment Variables and Known Issues. (#33623)
Enhancements
Added: Support for passing additional credential information in URL-Encoded Form (#33612)
ue-webservice 1.3.1 (2023-04-28)
Fixes
Fixed: STDOUT should include only the body of the webservice response (#32520)Fixed: Misleading warning message "...not designated as Output Only" is removed from UC logs (#32394)Fixed: Security Enhancements (#32631)
ue-webservice 1.3.0 (2023-03-23)
Enhancements
Added: Support for API Keys (#31456)Added: Support for retrieving OAuth 2.0 token using "Password Credentials" or "Client Credentials" grant and calling a Web Service within the same task (#31479)Added: Support for passing additional credential information as Query Parameters or as Headers (#31478)
ue-webservice 1.2.1 (2022-12-22)
Enhancements
Changed: The following Input Field Labels are improved to bring more context on the surrounding functionality (#31203):- Choice OAuth2Token in Authorization Type renamed to: Token
- Optional text field OAuthToken renamed to: Token
- Checkbox field Use SSL renamed to: SSL Options
- Checkbox field SSL Hostname Check renamed to: SSL Certificate Verification
- Optional text field Trusted Certificate File renamed to: CA Bundle Path
- Optional text field Public Key Certificate renamed to: Client Certificate Path
- Optional text field Private Key Certificate renamed to: Client Private Key Path
Changed: Payload input field is not mandatory anymore (#30639)
Up to ue-webservice-1.2.0, input field Payload was mandatory for HTTP Methods POST, PUT, PATCH. Starting from version 1.2.1 it is not necessary to provide data payload.
Fixes
Fixed: Field Pattern in Response Exit Code Mapping table is now evaluated as python regular expression, instead of a literal string (#31224)Fixed: Parse properly the JSON response when this is a list of objects (#30966)
ue-webservice 1.2.0 (2022-06-23)
Deprecations and Breaking Changes
Deprecated: "Print Result Body to" STDOUT functionality is intended to be used only for informational purposes. Users authoring workflows that read STDOUT from tasks originating from this Universal Template are encouraged to retrieve information from EXTENSION_OUTPUT instead of STDOUT to avoid disruptions. In future releases, the Response Body will be part only of EXTENSION_OUTPUT. (#28541)
Enhancements
Added: JSON body response formatted and printed in the Extension Output in new JSON attribute 'body_json' (#28541)
Fixes
Fixed: JSON body was not printed on STDOUT in certain cases of content-type combinations (#28080)
ue-webservice 1.1.0 (2022-03-10)
Enhancements
Added: Exit Code Mapping (#27233)Added: Print Response status on output only field (#26782)Added: Print Response Body in STDOUT (#26766)